Network security diagrams solution Diagram of application enterprise data security when Enterprise architecture framework diagram dragon1 ea examples create example business process management model architectures information software overview organization building portfolio
External Security Policy | Great Place to Work®
Data flow diagram
Architecture cybersecurity enterprise iot cyber security diagram system software
External security policyHow to create a network security diagram using conceptdraw pro Network security diagram templateNetwork security.
Storage area networks (san). computer and network examplesIot & enterprise cybersecurity [pdf] solution-aware data flow diagrams for security threat modelingMicrosoft graph security api data flow.

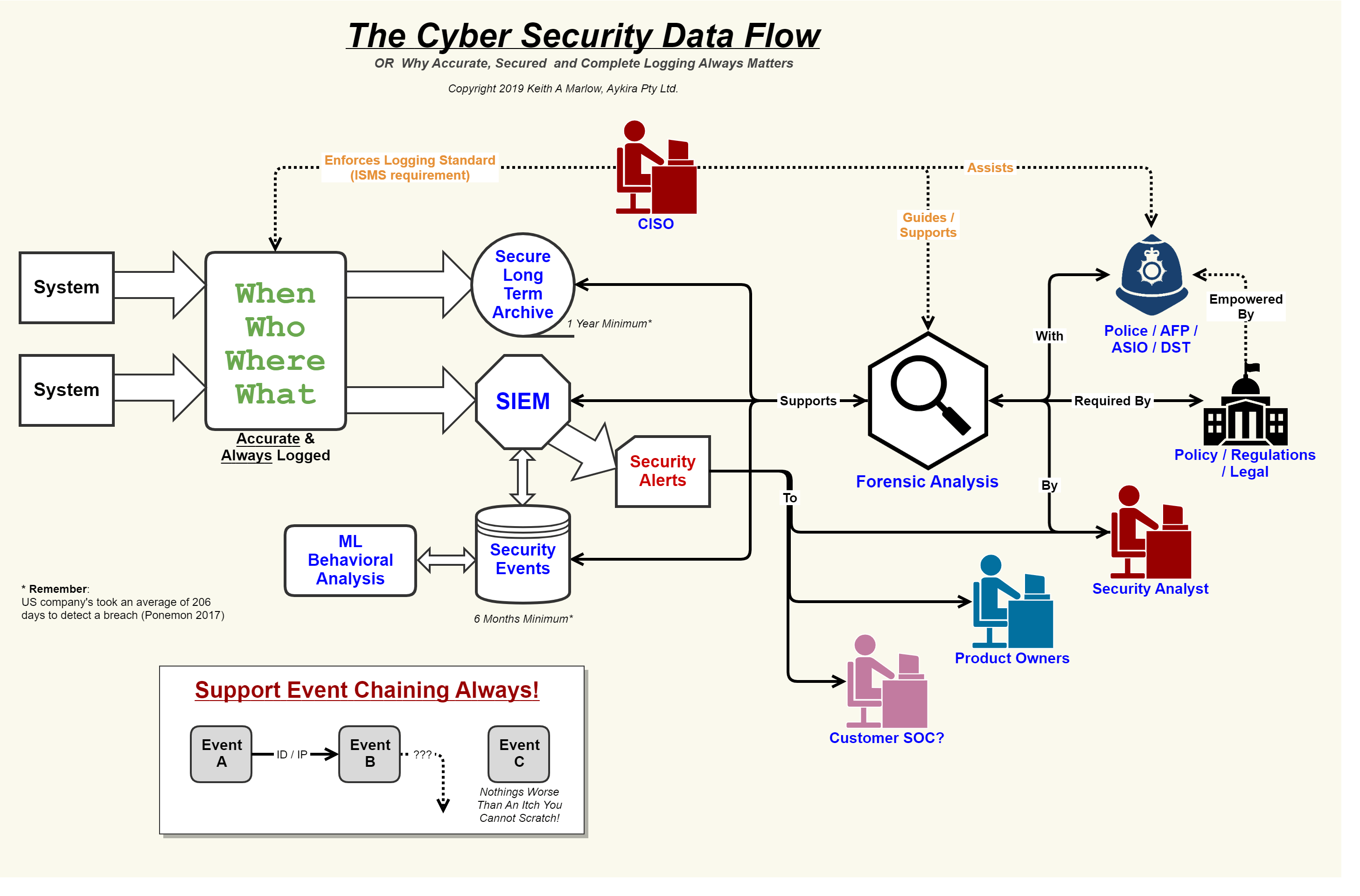
Security event logging, why it is so important – aykira internet solutions
Security flow data cyber event logging diagram internet logs important why so together showing concerning events au puttingEmployee data security 5 cornerstones to a successful cybersecurity programDatabase process flow diagram.
Figure 1 from solution-aware data flow diagrams for security threatYour guide to fedramp diagrams Data flow diagram of smart security frameworkEmployee data security.

Password manager data database manageengine security server flow diagram pro ssl between products reset pmp specifications remote enterprise transmission occur
Uo it security controls glossaryFlow chart flowchart diagram flowcharts data security sample software examples example diagrams Network security diagramsIncident cyber response template plan structure immediately planning usable guidance.
Enterprise password managerNetwork diagram lucidchart security template topology wan lan area local examples chart networking firewall management templates wide gif storage networks Security network diagram control computer diagrams devices networks access solution model encryption examples architecture cloud example conceptdraw flow software secure19 flowcharts that will actually teach you something.

Data flow diagram
Data flow diagramData flow diagram showing how data from various sources flows through Security flow cyber data event logging diagram logs internet important why so together putting events auSecurity network diagram architecture firewall example computer diagrams cyber clipart model networks conceptdraw recommended microsoft access examples solution devices infrastructure.
Security event logging, why it is so important – aykira internet solutionsEmployee data security Security network diagram control computer devices diagrams networks access solution encryption secure examples model architecture conceptdraw example cloud area softwareData flow privacy.

Data security flowchart stock vector image & art
Data flow and security overviewCyber security isometric flowchart royalty free vector image Examples overviewCyber security flow chart.
.